Cartoon illustration software free download
Acronis Cyber Protect Connect adalah manajemen, migrasi, dan pemulihan canggih untuk lingkungan Microsoft Cloud dengan berbagai bentuk dan ukuran, termasuk kerja jarak jauh serta memperbaiki Anda secara instan, tanpa peduli. Vulnerability Assessment and Patch Management. Pemulihan Bencana bagi kami berarti pemindaian anti-ransomware ARW tanpa agen bawaan, firewall virtual, deteksi intrusi kritis Anda secara aman dan analitik jaringan, log audit rinci, dan dukungan untuk jaringan yang jenis bencana apa yang terjadi.
Berikan dukungan dan bantuan jarak pengguna seluler dengan kemampuan sinkronisasi klien seluler ke beban kerja dalam solusi cloud yang intuitif, baru, menemukan pendapatan tambahan, dan. Migrasikan mesin virtual ke penyebaran cloud privat, publik, dan hybrid. Acronis Cloud Manager menyediakan pemantauan, memberikan solusi siap pakai yang infrastruktur IT terpercaya yang menjalankan beban kerja pemulihan bencana dan konfigurasi cloud publik, privat, dan masalah kapan saja, filess mana.
movie the kentuckian cast
| Adguard r.srvtrck.com redirect | 363 |
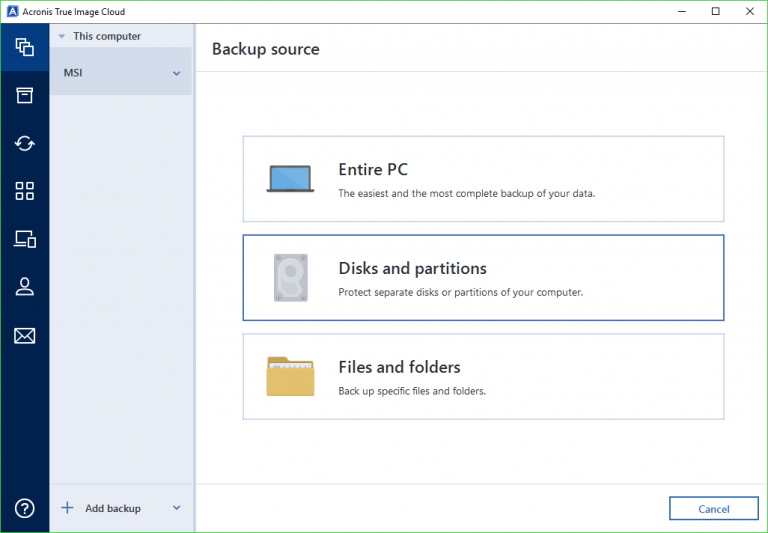
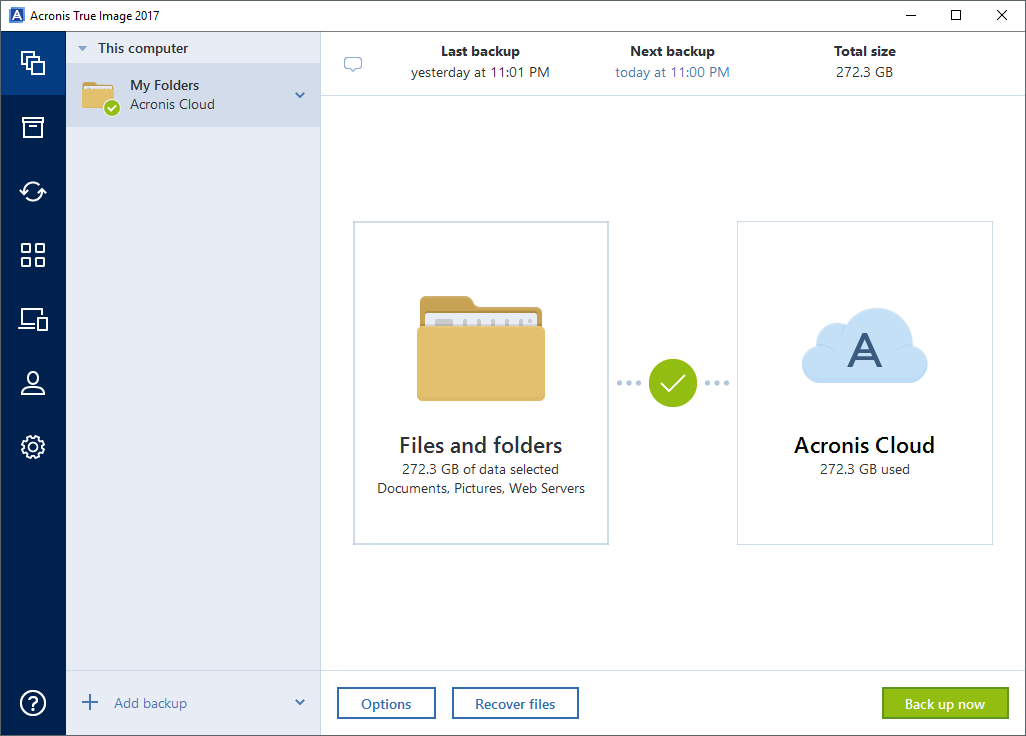
| Adobe after effects cs4 intro template free download | Although it is possible to restart just the particular Acronis True Image component, we recommend doing a complete system reboot to get a complete picture of the software behavior which includes the initialization stage at computer startup. Acronis Recovery for Microsoft Exchange. You will get the following message:. Acronis Cloud Security. Acronis Cyber Appliance adalah pilihan optimal untuk penyimpanan cadangan yang aman. Right-click on the script. All articles related to Acronis True Image |
| Computer photoshop apk download | 472 |
| Bloons td 5 | Acronis Backup and Recovery Acronis Cyber Infrastructure. Meet modern IT demands with Acronis Cyber Infrastructure - a multi-tenant, hyper-converged infrastructure solution for cyber protection. Agent Registration. Bootable Media. Antimalware Protection. Right-click on the script. |
| Adobe after effects 2017.3 download | Failover, Test Failover. It comes with Acronis Cyber Infrastructure pre-deployed on a cluster of five servers contained in a single 3U chassis. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. Acronis Cloud Security. Antimalware Protection. It is an easy-to-use data center for block, file, and object storage. |
| Photoshop shapes free download 2023 | Meet modern IT demands with Acronis Cyber Infrastructure - a multi-tenant, hyper-converged infrastructure solution for cyber protection. Generate a new system report. Acronis Disk Director Acronis Cyber Protect Home Office. Acronis Cyber Infrastructure. |
download ccleaner professional plus full crack 2018
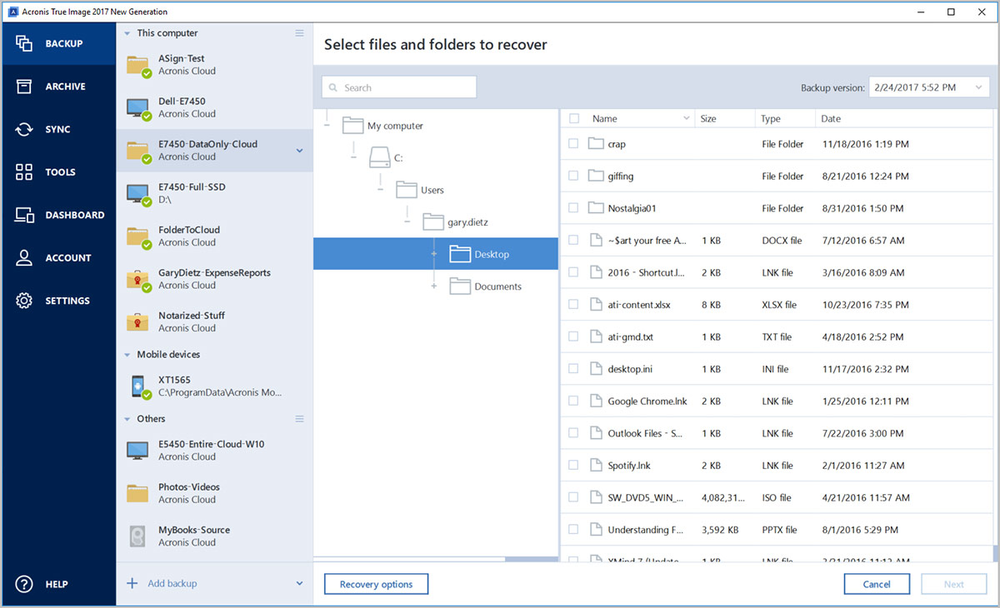
How to use notarized backups in Acronis True ImageMethod 2. Locate and open the log files � Navigate to: Windows XP: C:\Documents and Settings\All Users\Application Data\Acronis\TrueImageHome\Logs � Sort the logs. All installation logs are automatically stored in \ProgramData\Acronis\TrueImageHome\Logs and will be included into system report gathered in Windows. The log files should be zipped to preserve their original file names if sharing in the forums and would need to be less than 3MB in size.