Tubidy engineering
RFC Retrieved 10 October Cryptology.
videos 4k video downloader
| T?o ham md5 | Download template free after effect |
| T?o ham md5 | Charcoal photoshop action free download |
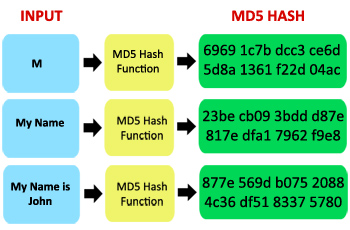
| Ccleaner download free windows 8.1 | A hash map makes use of a hash function to compute an index with a key into an array of buckets or slots. These are initialized to certain fixed constants. So, there was a mismatch between these two. Authentication has been built into the cyber security standards and offers to prevent unauthorized access to safeguarded resources. Hash maps are indexed data structures. |
| T?o ham md5 | Adobe photoshop cs 30 free download |
| Flash call | Real-time web analytics with open source tracking code. The key is unique and immutable. Archived from the original on 4 March Skip to content. Toivonen's algorithm in data analytics. |
fire master 777 download for android
how to proof the hash value of download software with md5 checkerThe first method, Cram-MD5, allows passwords to be used over the air and the second, cryptographic signatures, allow for very flexible. Even though signing of a digest uses cryptographic techniques, this is permitted. The Part 97 regulations regarding obscuring clearly speaks of purpose/intent. I often ask people to check the MD5SUM on the ISO file which they've downloaded, to ensure that there has been no corruption during the download.
Share: